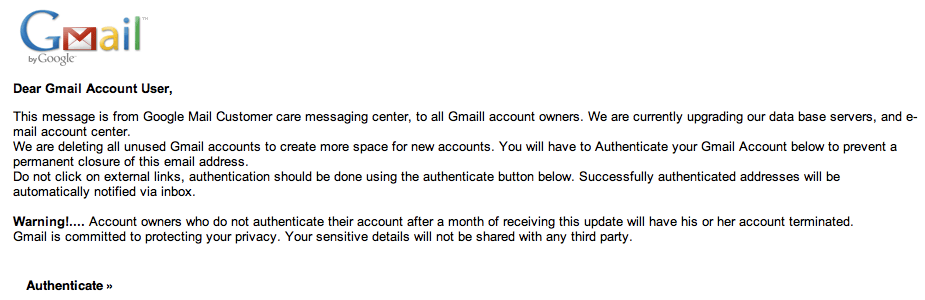
GMAIL PHISHER Full Version Free. A fake login page) for hacking Gmail. We are discus about how to make phishing page easily Phishing is use. Hello Friends in this hacking article today i will give you a sample of a Gmail phishing page which i made recently. So guys download it. Undetectable Phishing Method for Hack Someone’s Gmail Account; Tabnapping Method to hack Facebook and Gmail; This is a simple trick to hack any gmail password account by phishing page. You can also upload these files to your apache server. For any assistance about apache server go to my previous post. In any of free hosting servers. When you enter your username and password in Gmail login phishing page and click sign-in or hit enter the mail.php script is.
Gmail Phishing Code
Security researchers have discovered a new phishing campaign targeting Gmail users, which is so convincing and highly effective that even tech-savvy people can be tricked into giving away their Google credentials to hackers.
The attackers first compromise a victim's Gmail account, and once they are in, they start rifling through inboxes to launch secondary attacks in order to pass on the attack.
The hackers first look for an attachment that victims have previously sent to their contacts and a relevant subject from an actual sent email. Then the criminals will start gathering up contact email addresses, who become the new targets of the attackers.
After finding one, the hackers create an image (screenshot) of that attachment and include it in reply to the sender with the same or similar subject for the email, invoking recognition and automatic trust.
What makes this attack so effective is that the phishing emails come from someone the victim knows.
This new Gmail phishing attack uses image attachments that masquerade as a PDF file with a thumbnailed version of the attachment. Once clicked, victims are redirected to phishing pages, which disguise as the Google sign-in page. But it's a TRAP!
The URL of the fake Gmail login page contains the accounts.google.com subdomain, which is enough to fool the majority of people into believing that they are on a legitimate Google page.
Also, since the browser does not show the red warning icon usually used by Google to point out insecure pages, users fall for the Gmail hacking scheme.
Here's what WordFence CEO Mark Maunder who reported the attacks writes in a blog post:
Victims fall for the scam because of a clever trick employed by this attack, and they submit their credentials, which get delivered directly to the attackers. And as soon as the attackers get their credential, they log into the victim's Gmail account.
Protecting against this attack is very simple. Gmail users just need to enable two-factor authentication, and, of course, always be careful while opening any attachment in your email.
So even if the attackers have access to your credential, they’ll not be able to proceed further without your phone or a USB cryptographic key in order to access your account.
The attackers first compromise a victim's Gmail account, and once they are in, they start rifling through inboxes to launch secondary attacks in order to pass on the attack.
The hackers first look for an attachment that victims have previously sent to their contacts and a relevant subject from an actual sent email. Then the criminals will start gathering up contact email addresses, who become the new targets of the attackers.
After finding one, the hackers create an image (screenshot) of that attachment and include it in reply to the sender with the same or similar subject for the email, invoking recognition and automatic trust.
What makes this attack so effective is that the phishing emails come from someone the victim knows.
This new Gmail phishing attack uses image attachments that masquerade as a PDF file with a thumbnailed version of the attachment. Once clicked, victims are redirected to phishing pages, which disguise as the Google sign-in page. But it's a TRAP!
The URL of the fake Gmail login page contains the accounts.google.com subdomain, which is enough to fool the majority of people into believing that they are on a legitimate Google page.
Also, since the browser does not show the red warning icon usually used by Google to point out insecure pages, users fall for the Gmail hacking scheme.
Here's what WordFence CEO Mark Maunder who reported the attacks writes in a blog post:
'This phishing technique uses something called a ‘data URI’ to include a complete file in the browser location bar. When you glance up at the browser location bar and see ‘data:text/html…..’ that is actually a very long string of text.'
'In this [attack] the ‘data:text/html’ and the trusted hostname are the same color. That suggests to our perception that they’re related and the ‘data:text/html’ part either doesn’t matter or can be trusted.'
Victims fall for the scam because of a clever trick employed by this attack, and they submit their credentials, which get delivered directly to the attackers. And as soon as the attackers get their credential, they log into the victim's Gmail account.
Protecting against this attack is very simple. Gmail users just need to enable two-factor authentication, and, of course, always be careful while opening any attachment in your email.
So even if the attackers have access to your credential, they’ll not be able to proceed further without your phone or a USB cryptographic key in order to access your account.
Facebook Phishing Page
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.